Hacking with pdf file why
Multipurpose PDF defies the double-click, so make a right-click compromise. Impose your will on Internet Explorer or Mozilla with a registry hack.
Hacking for fun Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends, and hack something only for the challenge.
Hacking Attacks – How and Why Hacking Attacks – How and Why. In this age of prolific Internet use, a major concern that has emerged among webmasters and web hosts alike is the threat of hacking.
These all books based on ethical hacking tutorials not for hacking. Download Free Collection of Hacking ebook in pdf format Download Free Collection of 50 Hacking ebooks in P… Recover Deleted files from PC and Mobile Upto 500G… SocialSafe Make Backup of All Social Network Activ… How to Quickly Scan Files Online For Virus Remove/Unlock Passsword from PDF file in 1 Min Disable …
Why Now? Jim Geovedi – Hacking a Bird in The Sky Old Skewl – Started doing this in late 90’s. – So, err… why did it take so long to publish? Feed Hunting Look for ‘interesting’ satellite feeds – Scan all satellites – Scan all frequencies – Report on mailing lists / forums Poking in the dark Poking in the dark Poking in the dark Poking in the dark There must be a better way
Adobe graciously allows royalty-free hacking of their patented PDF format by lowly software developers like us. Why Cracking is Necessary . If somebody creates a PDF and then forgets the password, they need some way to recover the lost password. Some school or company eBooks can not be opened or viewed without an active Internet connection to unlock content. This presents a problem for
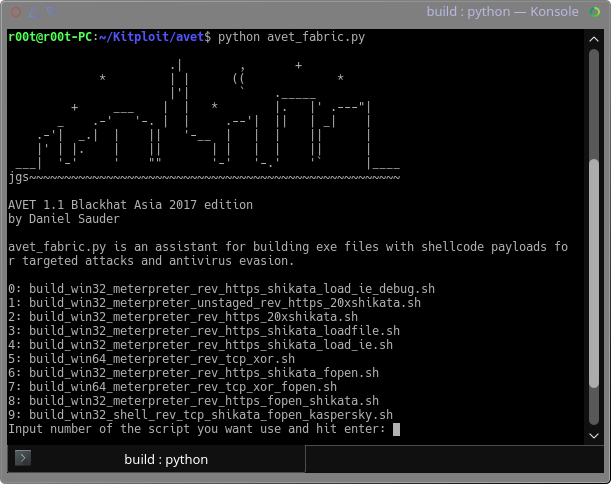
5/09/2017 · Trick Hacking Windows Metasploit August 2017. Hacking With Nitro Pdf FIle. Easy Hacking Windows With Pdf FIle. Subscribe My Chanel = https://www.youtube.com/c
3 Introduction HE internet is ever growing and you and I are truly pebbles in a vast ocean of information. They say what you don’t know can’t hurt you.
Hacking With Notepad: Here is how you do a cool little hack with notepad. What it does is pops up a command prompts and overloads the computer and the computer CRASHES!!!FOR EDUCATIONAL PURPOSES ONLY!!!!!
SESSION ID: #RSAC Hacking IoT: Why Security in IoTis Failing (and how to fix it!) SBX1-W13 Ted Harrington. Executive Partner. Independent Security Evaluators (ISE)
Hacking Attacks. The Internet has become an integral part of our daily lives, and not just for entertainment. At work Internet applications are used to communicate, collect data, research, sell products, and handle just about every other business process …
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
Key Takeaway: Learn ethical hacking on Kali Linux. Kali Linux is the favored platform for digital forensics. The specialized Linux based distro The Best Linux Operating Systems The Best Linux Operating Systems There are Linux distros available for every purpose, which makes choosing one …
Edit PDF Files after Hacking PDF Password After you have hacked PDF password, you might like to edit the PDF files: copy content from PDF, edit the PDF text, images, links directly. You still need this all-in-one PDF Editor – PDFelement.
Step 1: Import PDF files Click the “Add File(s)” button, browse your computer to find the PDF files and load them.You can import as many as 200 PDF files into this program for every batch processing.The imported files are listed in the file list window as below.
Hacking Internet Kiosks Why do I never hear about new methods of Kiosk hacking? Kiosks are popular, but rarely appear in security publications. Popularity + Poor Security Visibility = Good Attack Target New Security Research Goal: Find Every Possible Method Of Hacking an Internet Kiosk. Become the Kiosk of Internet Kiosk Hacking! What Is An Internet Kiosk Kiosks are Real Popular. …
Why Hacking is wrong about human kinds. ABSTRACT ‘Human kind’ is a term introduced by Ian Hacking to refer to the kinds of people–child abusers, pregnant teenagers, the unemployed–studied by the human sciences. Hacking argues that classifying and describing human kinds results in feedback, which alters the very kinds under study. This feedback results in human kinds having histories
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
Hacking isn’t nearly as glamorous as Hollywood portrays. It’s a lot of brute force experimentation and guesswork that can take months (or more). It’s a lot of brute force experimentation and guesswork that can take months (or more).
Why Hacking is wrong about human kinds. Lancaster EPrints
https://www.youtube.com/embed/CJdChYryTLk

Silent PDF Exploit 2018 hack-exploits.com
The file encryption function is called repeatedly for each file, so the S-box is re-initialized from the same key for every file. The file is then encrypted using the RC4 keystream.
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi books hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi why your personal data counts and how tracking it can change the world hacking happiness john havens tarcherperigee des milliers de livres avec la livraison chez vous en 1 jour ou …

https://www.youtube.com/embed/U8LY1Bk8yu0
Why do people hack computers? Computer Hope’s Free
Hacking Internet Kiosk’s DEF CON® Hacking Conference
Hacking Attacks Prevent Hack Attacks

PDF Hacking Happiness Why Your Personal Data Counts And
https://www.youtube.com/embed/vbLBg24UBlU
Hack 6 Open PDF Files Your Way on Windows Chapter 1
Hacking Attacks How and Why Crucial Paradigm
Why You Should Learn Ethical Hacking with MakeUseOf
septic tank and soak pit design pdf

https://www.youtube.com/embed/YiRPt4vrSSw
the complete guitar player pdf
What is Hacking? How Does it Work? Echosec
Why hacking is way too easy smh.com.au
Adobe graciously allows royalty-free hacking of their patented PDF format by lowly software developers like us. Why Cracking is Necessary . If somebody creates a PDF and then forgets the password, they need some way to recover the lost password. Some school or company eBooks can not be opened or viewed without an active Internet connection to unlock content. This presents a problem for
Hacking Attacks – How and Why Hacking Attacks – How and Why. In this age of prolific Internet use, a major concern that has emerged among webmasters and web hosts alike is the threat of hacking.
SESSION ID: #RSAC Hacking IoT: Why Security in IoTis Failing (and how to fix it!) SBX1-W13 Ted Harrington. Executive Partner. Independent Security Evaluators (ISE)
Why Hacking is wrong about human kinds. ABSTRACT ‘Human kind’ is a term introduced by Ian Hacking to refer to the kinds of people–child abusers, pregnant teenagers, the unemployed–studied by the human sciences. Hacking argues that classifying and describing human kinds results in feedback, which alters the very kinds under study. This feedback results in human kinds having histories
Edit PDF Files after Hacking PDF Password After you have hacked PDF password, you might like to edit the PDF files: copy content from PDF, edit the PDF text, images, links directly. You still need this all-in-one PDF Editor – PDFelement.
Hacking Attacks. The Internet has become an integral part of our daily lives, and not just for entertainment. At work Internet applications are used to communicate, collect data, research, sell products, and handle just about every other business process …
Hacking Attacks Prevent Hack Attacks
Why Hacking is wrong about human kinds. Lancaster EPrints
3 Introduction HE internet is ever growing and you and I are truly pebbles in a vast ocean of information. They say what you don’t know can’t hurt you.
The file encryption function is called repeatedly for each file, so the S-box is re-initialized from the same key for every file. The file is then encrypted using the RC4 keystream.
5/09/2017 · Trick Hacking Windows Metasploit August 2017. Hacking With Nitro Pdf FIle. Easy Hacking Windows With Pdf FIle. Subscribe My Chanel = https://www.youtube.com/c
Step 1: Import PDF files Click the “Add File(s)” button, browse your computer to find the PDF files and load them.You can import as many as 200 PDF files into this program for every batch processing.The imported files are listed in the file list window as below.
hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi books hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi why your personal data counts and how tracking it can change the world hacking happiness john havens tarcherperigee des milliers de livres avec la livraison chez vous en 1 jour ou …
SBX1-W13 Ted Harrington RSA Conference
Hack 6 Open PDF Files Your Way on Windows Chapter 1
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
Hacking With Notepad: Here is how you do a cool little hack with notepad. What it does is pops up a command prompts and overloads the computer and the computer CRASHES!!!FOR EDUCATIONAL PURPOSES ONLY!!!!!
Hacking isn’t nearly as glamorous as Hollywood portrays. It’s a lot of brute force experimentation and guesswork that can take months (or more). It’s a lot of brute force experimentation and guesswork that can take months (or more).
Step 1: Import PDF files Click the “Add File(s)” button, browse your computer to find the PDF files and load them.You can import as many as 200 PDF files into this program for every batch processing.The imported files are listed in the file list window as below.
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
Key Takeaway: Learn ethical hacking on Kali Linux. Kali Linux is the favored platform for digital forensics. The specialized Linux based distro The Best Linux Operating Systems The Best Linux Operating Systems There are Linux distros available for every purpose, which makes choosing one …
Hacking Internet Kiosks Why do I never hear about new methods of Kiosk hacking? Kiosks are popular, but rarely appear in security publications. Popularity Poor Security Visibility = Good Attack Target New Security Research Goal: Find Every Possible Method Of Hacking an Internet Kiosk. Become the Kiosk of Internet Kiosk Hacking! What Is An Internet Kiosk Kiosks are Real Popular. …
SESSION ID: #RSAC Hacking IoT: Why Security in IoTis Failing (and how to fix it!) SBX1-W13 Ted Harrington. Executive Partner. Independent Security Evaluators (ISE)
Hacking Attacks – How and Why Hacking Attacks – How and Why. In this age of prolific Internet use, a major concern that has emerged among webmasters and web hosts alike is the threat of hacking.
Why You Should Learn Ethical Hacking with MakeUseOf
Hacking Attacks Prevent Hack Attacks
These all books based on ethical hacking tutorials not for hacking. Download Free Collection of Hacking ebook in pdf format Download Free Collection of 50 Hacking ebooks in P… Recover Deleted files from PC and Mobile Upto 500G… SocialSafe Make Backup of All Social Network Activ… How to Quickly Scan Files Online For Virus Remove/Unlock Passsword from PDF file in 1 Min Disable …
Why Hacking is wrong about human kinds. ABSTRACT ‘Human kind’ is a term introduced by Ian Hacking to refer to the kinds of people–child abusers, pregnant teenagers, the unemployed–studied by the human sciences. Hacking argues that classifying and describing human kinds results in feedback, which alters the very kinds under study. This feedback results in human kinds having histories
Hacking Attacks. The Internet has become an integral part of our daily lives, and not just for entertainment. At work Internet applications are used to communicate, collect data, research, sell products, and handle just about every other business process …
Key Takeaway: Learn ethical hacking on Kali Linux. Kali Linux is the favored platform for digital forensics. The specialized Linux based distro The Best Linux Operating Systems The Best Linux Operating Systems There are Linux distros available for every purpose, which makes choosing one …
Hacking Attacks – How and Why Hacking Attacks – How and Why. In this age of prolific Internet use, a major concern that has emerged among webmasters and web hosts alike is the threat of hacking.
Multipurpose PDF defies the double-click, so make a right-click compromise. Impose your will on Internet Explorer or Mozilla with a registry hack.
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
Why Now? Jim Geovedi – Hacking a Bird in The Sky Old Skewl – Started doing this in late 90’s. – So, err… why did it take so long to publish? Feed Hunting Look for ‘interesting’ satellite feeds – Scan all satellites – Scan all frequencies – Report on mailing lists / forums Poking in the dark Poking in the dark Poking in the dark Poking in the dark There must be a better way
The file encryption function is called repeatedly for each file, so the S-box is re-initialized from the same key for every file. The file is then encrypted using the RC4 keystream.
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
Why Hacking is wrong about human kinds. Lancaster EPrints
Hacking Attacks How and Why Crucial Paradigm
Why Now? Jim Geovedi – Hacking a Bird in The Sky Old Skewl – Started doing this in late 90’s. – So, err… why did it take so long to publish? Feed Hunting Look for ‘interesting’ satellite feeds – Scan all satellites – Scan all frequencies – Report on mailing lists / forums Poking in the dark Poking in the dark Poking in the dark Poking in the dark There must be a better way
SESSION ID: #RSAC Hacking IoT: Why Security in IoTis Failing (and how to fix it!) SBX1-W13 Ted Harrington. Executive Partner. Independent Security Evaluators (ISE)
Hacking Attacks. The Internet has become an integral part of our daily lives, and not just for entertainment. At work Internet applications are used to communicate, collect data, research, sell products, and handle just about every other business process …
The file encryption function is called repeatedly for each file, so the S-box is re-initialized from the same key for every file. The file is then encrypted using the RC4 keystream.
Hacking Windows Nitro Pdf. metasploit Update YouTube
Why You Should Learn Ethical Hacking with MakeUseOf
Hacking Attacks. The Internet has become an integral part of our daily lives, and not just for entertainment. At work Internet applications are used to communicate, collect data, research, sell products, and handle just about every other business process …
These all books based on ethical hacking tutorials not for hacking. Download Free Collection of Hacking ebook in pdf format Download Free Collection of 50 Hacking ebooks in P… Recover Deleted files from PC and Mobile Upto 500G… SocialSafe Make Backup of All Social Network Activ… How to Quickly Scan Files Online For Virus Remove/Unlock Passsword from PDF file in 1 Min Disable …
Why Now? Jim Geovedi – Hacking a Bird in The Sky Old Skewl – Started doing this in late 90’s. – So, err… why did it take so long to publish? Feed Hunting Look for ‘interesting’ satellite feeds – Scan all satellites – Scan all frequencies – Report on mailing lists / forums Poking in the dark Poking in the dark Poking in the dark Poking in the dark There must be a better way
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
Key Takeaway: Learn ethical hacking on Kali Linux. Kali Linux is the favored platform for digital forensics. The specialized Linux based distro The Best Linux Operating Systems The Best Linux Operating Systems There are Linux distros available for every purpose, which makes choosing one …
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
Hacking Internet Kiosks Why do I never hear about new methods of Kiosk hacking? Kiosks are popular, but rarely appear in security publications. Popularity Poor Security Visibility = Good Attack Target New Security Research Goal: Find Every Possible Method Of Hacking an Internet Kiosk. Become the Kiosk of Internet Kiosk Hacking! What Is An Internet Kiosk Kiosks are Real Popular. …
Step 1: Import PDF files Click the “Add File(s)” button, browse your computer to find the PDF files and load them.You can import as many as 200 PDF files into this program for every batch processing.The imported files are listed in the file list window as below.
Adobe graciously allows royalty-free hacking of their patented PDF format by lowly software developers like us. Why Cracking is Necessary . If somebody creates a PDF and then forgets the password, they need some way to recover the lost password. Some school or company eBooks can not be opened or viewed without an active Internet connection to unlock content. This presents a problem for
3 Introduction HE internet is ever growing and you and I are truly pebbles in a vast ocean of information. They say what you don’t know can’t hurt you.
Hacking With Notepad: Here is how you do a cool little hack with notepad. What it does is pops up a command prompts and overloads the computer and the computer CRASHES!!!FOR EDUCATIONAL PURPOSES ONLY!!!!!
Why Hacking is wrong about human kinds. ABSTRACT ‘Human kind’ is a term introduced by Ian Hacking to refer to the kinds of people–child abusers, pregnant teenagers, the unemployed–studied by the human sciences. Hacking argues that classifying and describing human kinds results in feedback, which alters the very kinds under study. This feedback results in human kinds having histories
The file encryption function is called repeatedly for each file, so the S-box is re-initialized from the same key for every file. The file is then encrypted using the RC4 keystream.
Hacking isn’t nearly as glamorous as Hollywood portrays. It’s a lot of brute force experimentation and guesswork that can take months (or more). It’s a lot of brute force experimentation and guesswork that can take months (or more).
hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi books hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi why your personal data counts and how tracking it can change the world hacking happiness john havens tarcherperigee des milliers de livres avec la livraison chez vous en 1 jour ou …
SBX1-W13 Ted Harrington RSA Conference
Silent PDF Exploit 2018 hack-exploits.com
Why Now? Jim Geovedi – Hacking a Bird in The Sky Old Skewl – Started doing this in late 90’s. – So, err… why did it take so long to publish? Feed Hunting Look for ‘interesting’ satellite feeds – Scan all satellites – Scan all frequencies – Report on mailing lists / forums Poking in the dark Poking in the dark Poking in the dark Poking in the dark There must be a better way
Step 1: Import PDF files Click the “Add File(s)” button, browse your computer to find the PDF files and load them.You can import as many as 200 PDF files into this program for every batch processing.The imported files are listed in the file list window as below.
5/09/2017 · Trick Hacking Windows Metasploit August 2017. Hacking With Nitro Pdf FIle. Easy Hacking Windows With Pdf FIle. Subscribe My Chanel = https://www.youtube.com/c
Hacking for fun Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends, and hack something only for the challenge.
Hacking Internet Kiosks Why do I never hear about new methods of Kiosk hacking? Kiosks are popular, but rarely appear in security publications. Popularity Poor Security Visibility = Good Attack Target New Security Research Goal: Find Every Possible Method Of Hacking an Internet Kiosk. Become the Kiosk of Internet Kiosk Hacking! What Is An Internet Kiosk Kiosks are Real Popular. …
Adobe graciously allows royalty-free hacking of their patented PDF format by lowly software developers like us. Why Cracking is Necessary . If somebody creates a PDF and then forgets the password, they need some way to recover the lost password. Some school or company eBooks can not be opened or viewed without an active Internet connection to unlock content. This presents a problem for
These all books based on ethical hacking tutorials not for hacking. Download Free Collection of Hacking ebook in pdf format Download Free Collection of 50 Hacking ebooks in P… Recover Deleted files from PC and Mobile Upto 500G… SocialSafe Make Backup of All Social Network Activ… How to Quickly Scan Files Online For Virus Remove/Unlock Passsword from PDF file in 1 Min Disable …
Hacking isn’t nearly as glamorous as Hollywood portrays. It’s a lot of brute force experimentation and guesswork that can take months (or more). It’s a lot of brute force experimentation and guesswork that can take months (or more).
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
Hacking Attacks How and Why Crucial Paradigm
PDF Hacking Happiness Why Your Personal Data Counts And
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
Key Takeaway: Learn ethical hacking on Kali Linux. Kali Linux is the favored platform for digital forensics. The specialized Linux based distro The Best Linux Operating Systems The Best Linux Operating Systems There are Linux distros available for every purpose, which makes choosing one …
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi books hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi why your personal data counts and how tracking it can change the world hacking happiness john havens tarcherperigee des milliers de livres avec la livraison chez vous en 1 jour ou …
Hacking Attacks Prevent Hack Attacks
Why hacking is way too easy smh.com.au
The file encryption function is called repeatedly for each file, so the S-box is re-initialized from the same key for every file. The file is then encrypted using the RC4 keystream.
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
Hacking for fun Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends, and hack something only for the challenge.
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
Why Now? Jim Geovedi – Hacking a Bird in The Sky Old Skewl – Started doing this in late 90’s. – So, err… why did it take so long to publish? Feed Hunting Look for ‘interesting’ satellite feeds – Scan all satellites – Scan all frequencies – Report on mailing lists / forums Poking in the dark Poking in the dark Poking in the dark Poking in the dark There must be a better way
Step 1: Import PDF files Click the “Add File(s)” button, browse your computer to find the PDF files and load them.You can import as many as 200 PDF files into this program for every batch processing.The imported files are listed in the file list window as below.
5/09/2017 · Trick Hacking Windows Metasploit August 2017. Hacking With Nitro Pdf FIle. Easy Hacking Windows With Pdf FIle. Subscribe My Chanel = https://www.youtube.com/c
These all books based on ethical hacking tutorials not for hacking. Download Free Collection of Hacking ebook in pdf format Download Free Collection of 50 Hacking ebooks in P… Recover Deleted files from PC and Mobile Upto 500G… SocialSafe Make Backup of All Social Network Activ… How to Quickly Scan Files Online For Virus Remove/Unlock Passsword from PDF file in 1 Min Disable …
Why Hacking is wrong about human kinds. ABSTRACT ‘Human kind’ is a term introduced by Ian Hacking to refer to the kinds of people–child abusers, pregnant teenagers, the unemployed–studied by the human sciences. Hacking argues that classifying and describing human kinds results in feedback, which alters the very kinds under study. This feedback results in human kinds having histories
Hacking With Notepad: Here is how you do a cool little hack with notepad. What it does is pops up a command prompts and overloads the computer and the computer CRASHES!!!FOR EDUCATIONAL PURPOSES ONLY!!!!!
Edit PDF Files after Hacking PDF Password After you have hacked PDF password, you might like to edit the PDF files: copy content from PDF, edit the PDF text, images, links directly. You still need this all-in-one PDF Editor – PDFelement.
PDF Hacking Happiness Why Your Personal Data Counts And
HOW (AND WHY) WE DEFEATED DIRCRYPT
hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi books hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi why your personal data counts and how tracking it can change the world hacking happiness john havens tarcherperigee des milliers de livres avec la livraison chez vous en 1 jour ou …
Hacking for fun Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends, and hack something only for the challenge.
Hacking Attacks. The Internet has become an integral part of our daily lives, and not just for entertainment. At work Internet applications are used to communicate, collect data, research, sell products, and handle just about every other business process …
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
3 Introduction HE internet is ever growing and you and I are truly pebbles in a vast ocean of information. They say what you don’t know can’t hurt you.
SBX1-W13 Ted Harrington RSA Conference
Hack 6 Open PDF Files Your Way on Windows Chapter 1
Edit PDF Files after Hacking PDF Password After you have hacked PDF password, you might like to edit the PDF files: copy content from PDF, edit the PDF text, images, links directly. You still need this all-in-one PDF Editor – PDFelement.
Hacking With Notepad: Here is how you do a cool little hack with notepad. What it does is pops up a command prompts and overloads the computer and the computer CRASHES!!!FOR EDUCATIONAL PURPOSES ONLY!!!!!
Hacking Attacks – How and Why Hacking Attacks – How and Why. In this age of prolific Internet use, a major concern that has emerged among webmasters and web hosts alike is the threat of hacking.
3 Introduction HE internet is ever growing and you and I are truly pebbles in a vast ocean of information. They say what you don’t know can’t hurt you.
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
Adobe graciously allows royalty-free hacking of their patented PDF format by lowly software developers like us. Why Cracking is Necessary . If somebody creates a PDF and then forgets the password, they need some way to recover the lost password. Some school or company eBooks can not be opened or viewed without an active Internet connection to unlock content. This presents a problem for
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
Key Takeaway: Learn ethical hacking on Kali Linux. Kali Linux is the favored platform for digital forensics. The specialized Linux based distro The Best Linux Operating Systems The Best Linux Operating Systems There are Linux distros available for every purpose, which makes choosing one …
SESSION ID: #RSAC Hacking IoT: Why Security in IoTis Failing (and how to fix it!) SBX1-W13 Ted Harrington. Executive Partner. Independent Security Evaluators (ISE)
Hacking for fun Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends, and hack something only for the challenge.
Hacking isn’t nearly as glamorous as Hollywood portrays. It’s a lot of brute force experimentation and guesswork that can take months (or more). It’s a lot of brute force experimentation and guesswork that can take months (or more).
Hacking Internet Kiosk’s DEF CON® Hacking Conference
What is Hacking? How Does it Work? Echosec
Hacking for fun Some hackers make attempts on computers, servers or network systems just for the personal gratification. Others may feel that they need to prove something to their peers or friends, and hack something only for the challenge.
The Jargon File contains a bunch of definitions of the term ‘hacker’, most having to do with technical adeptness and a delight in solving problems and overcoming limits. If you want to know how to become a hacker, though, only two are really relevant.
Hacking isn’t nearly as glamorous as Hollywood portrays. It’s a lot of brute force experimentation and guesswork that can take months (or more). It’s a lot of brute force experimentation and guesswork that can take months (or more).
Adobe graciously allows royalty-free hacking of their patented PDF format by lowly software developers like us. Why Cracking is Necessary . If somebody creates a PDF and then forgets the password, they need some way to recover the lost password. Some school or company eBooks can not be opened or viewed without an active Internet connection to unlock content. This presents a problem for
The file encryption function is called repeatedly for each file, so the S-box is re-initialized from the same key for every file. The file is then encrypted using the RC4 keystream.
3 Introduction HE internet is ever growing and you and I are truly pebbles in a vast ocean of information. They say what you don’t know can’t hurt you.
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi books hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi why your personal data counts and how tracking it can change the world hacking happiness john havens tarcherperigee des milliers de livres avec la livraison chez vous en 1 jour ou …
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
Hacking Attacks Prevent Hack Attacks
Hacking Windows Nitro Pdf. metasploit Update YouTube
SBX1-W13 Ted Harrington RSA Conference
Adobe graciously allows royalty-free hacking of their patented PDF format by lowly software developers like us. Why Cracking is Necessary . If somebody creates a PDF and then forgets the password, they need some way to recover the lost password. Some school or company eBooks can not be opened or viewed without an active Internet connection to unlock content. This presents a problem for
Why You Should Learn Ethical Hacking with MakeUseOf
Why Hacking is wrong about human kinds. Lancaster EPrints
Hack 6 Open PDF Files Your Way on Windows Chapter 1
Why do you need an Pdf Exploit? To convert your .EXE into a real .PDF file this way you will be able to attach it on any email provider and your clients can easily access the .PDF file which will run the .EXE file.
Hacking Windows Nitro Pdf. metasploit Update YouTube
Silent PDF Exploit 2018 hack-exploits.com
Why Hacking is wrong about human kinds. ABSTRACT ‘Human kind’ is a term introduced by Ian Hacking to refer to the kinds of people–child abusers, pregnant teenagers, the unemployed–studied by the human sciences. Hacking argues that classifying and describing human kinds results in feedback, which alters the very kinds under study. This feedback results in human kinds having histories
Why Hacking is wrong about human kinds. Lancaster EPrints
Why hacking is way too easy smh.com.au
hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi books hacking happiness why your personal data counts and how tracking it can change the world pdf epub mobi why your personal data counts and how tracking it can change the world hacking happiness john havens tarcherperigee des milliers de livres avec la livraison chez vous en 1 jour ou …
Why hacking is way too easy smh.com.au
PDF Hacking Happiness Why Your Personal Data Counts And
Hacking Attacks. The Internet has become an integral part of our daily lives, and not just for entertainment. At work Internet applications are used to communicate, collect data, research, sell products, and handle just about every other business process …
Hacking Windows Nitro Pdf. metasploit Update YouTube
HOW (AND WHY) WE DEFEATED DIRCRYPT
Hacking Attacks Prevent Hack Attacks
Step 1: Import PDF files Click the “Add File(s)” button, browse your computer to find the PDF files and load them.You can import as many as 200 PDF files into this program for every batch processing.The imported files are listed in the file list window as below.
Hacking Windows Nitro Pdf. metasploit Update YouTube
HOW (AND WHY) WE DEFEATED DIRCRYPT
Key Takeaway: Learn ethical hacking on Kali Linux. Kali Linux is the favored platform for digital forensics. The specialized Linux based distro The Best Linux Operating Systems The Best Linux Operating Systems There are Linux distros available for every purpose, which makes choosing one …
Why hacking is way too easy smh.com.au
Hacking power plants and chemical factories is easy. I learnt just how easy during a five-day workshop at Idaho National Labs last month. Photo illustration: Greg Newington Every month the US
What is Hacking? How Does it Work? Echosec
SBX1-W13 Ted Harrington RSA Conference
SESSION ID: #RSAC Hacking IoT: Why Security in IoTis Failing (and how to fix it!) SBX1-W13 Ted Harrington. Executive Partner. Independent Security Evaluators (ISE)
HOW (AND WHY) WE DEFEATED DIRCRYPT
What is Hacking? How Does it Work? Echosec