Ikev2 ipsec virtual private network pdf
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN lient’s underlying OS.
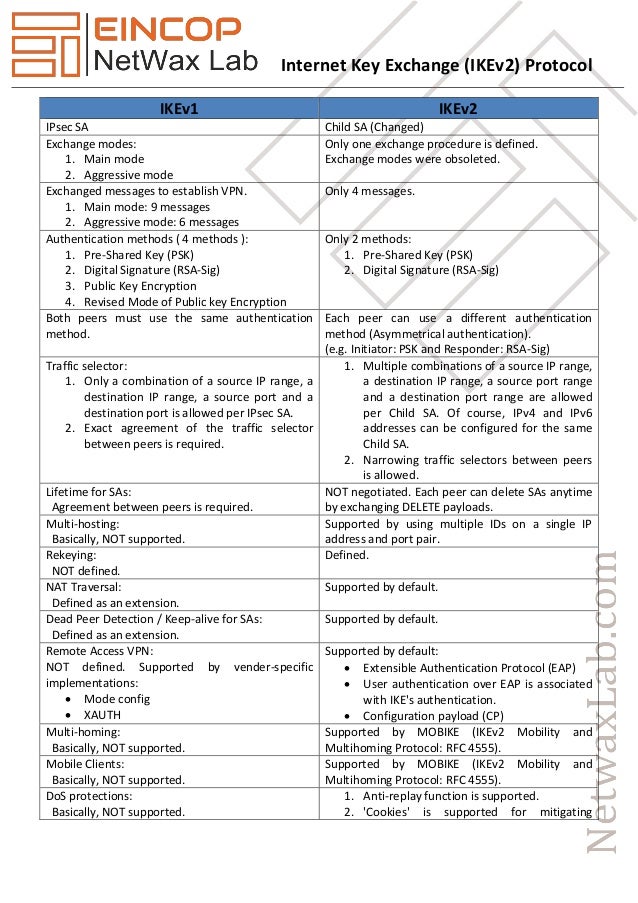
Using IPSec, you can create virtual private networks (VPNs) – z/OS IKEv2 support does not include Network Address Translation (NAT) • Continue to use IKEv1 if there is a NAT between the security endpoints – z/OS IKEv2 support does not include support for Sysplex-Wide Security Associations (SWSA) • Continue to use IKEv1 for SWSA in your sysplex Coming in z/OS V1R13 – …
If you are new to the basic concepts of VPN (Virtual Private Network) and IPSec, please learn following lessons before continuing. What is VPN (Virtual Private Network)
Virtual Private Network User Guide 1 Overview Issue 05 (2017-08-30) 5 Protocol Description Constraint negotiation. RFC 4301 Defines the IPsec architecture, the security
Internet Protocol Security (IPSec) is a suite of protocols that provide network-layer security to a Virtual Private Network (VPN). A VPN is a virtual network connection that provides a secure communication path between two peers in a public network.
A Virtual Private Network (VPN) provides a secure connection between two or more computers or protected networks over the public Internet. It provides authentication to ensure that the information is going to and from the correct parties. It provides security to protect the information from viewing or tampering en route.
GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to
A virtual private network, or VPN, allows you to securely encrypt traffic as it travels through untrusted networks, such as those at the coffee shop, a conference, or an airport. IKEv2 , or Internet Key Exchange v2, is a protocol that allows for direct IPSec tunneling between the server and client.
DOWNLOAD IKEV2 IPSEC VIRTUAL PRIVATE NETWORKS UNDERSTANDING AND ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer
Download a technical guide to ipsec virtual private networks or read online here in PDF or EPUB. Please click button to get a technical guide to ipsec virtual private networks book now. All books are in clear copy here, and all files are secure so don’t worry about it.
IKEv2 IPsec Virtual Private Networks Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS Graham Bartlett, CCIE No. 26709 Amjad Inamdar, CISSP No. 460898
IKEv2 vpn client setup on linux FIshVPN 19 Nov 2017 NetworkManager is a program for providing detection and configuration for systems to automatically connect to network.NetworkManager allows configuration and control of VPN daemons through a plugin interface.
You can use IKEv2 as a virtual private network (VPN) tunneling protocol that supports automatic VPN reconnection. IKEv2 allows the security association to remain unchanged despite changes in the underlying connection.
IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs). IPsec VPN overview provides a brief overview of IPsec technology and includes general information about how to
This sample chapter defines virtual private networks (VPNs) and explores fundamental Internet Protocol Security (IPSec) technologies. This chapter also covers IPSec crypto components, an overview of IKE, IPSec security, and a certificate authority (CA) support overview.
Internet Protocol Security (IPsec) NETWORK SMARTER
https://www.youtube.com/embed/Z7LwU6H5IGE

Support of NAT traversal in IKEv2 implementation
A Virtual Private Network (VPN) provides a secure connection between two or more computers or protected networks over the public internet. It provides authentication to ensure that the information is going to and from the correct parties. It provides security to protect the information from viewing or tampering en route. Prior to the invention of Internet Protocol Security (IPSec) and Secure
In the typical case, a mobile host establishes a Virtual Private Network (VPN) with a security gateway on its home network and requests that it be given an IP address on the home network. ( Note: This eliminates one of the problems that the combined use of Layer 2 Tunneling Protocol (L2TP) and IPsec is intended to solve.)
Free – GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco Sat, 03 Nov 2018 12:08:00 GMT Ikev2 Ipsec Virtual Private Networks Pearsoncmg – autowp.org – Click Download or
Specify the Local Network and Remote Network so that the traffic between these networks are encrypted and passed through the VPN tunnel. 5. 5. Click Manage. ♦ IPsec Proposal in IKEv2 is synonymous to the Transform Set in IKEv1.. in order to modify the IKE policy.
network attributes like virtual IP addresses and internal DNS information). We will also give an outlook on our forthcoming “Peer-to-Peer NAT- Traversal for IPsec” Internet draft which proposes an innovative IKEv2
Virtual Private Networks Page 1-3 Go to Table of Contents them to the destination terminal. (To perform tunnel termination, the device must maintain a table of …
ikev2 ipsec virtual private networks pearsoncmg Fri, 07 Dec 2018 10:31:00 GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private
The most secure way to browse on a public network is to use a virtual private network. A VPN provides a secure and private way to connect to open networks. A VPN provides a secure and private way to connect to open networks.
inside of a private network, and provides a secure tunnel to a VPN Gateway. The tunnel provides The tunnel provides confidentiality, integrity, and data authentication for information that travels across the public network.
Network Security Lecture 3 Design and Analysis of Communication Networks (DACS) University of Twente The Netherlands . Security protocols application transport network datalink physical . Contents • IPSec overview • IPSec in practice • IPSec standardization • IPSec modes: transport – tunnel • IPSec AH • IPSec ESP • IPSec and VPNs • IPSec key management • Summary . Contents
create a virtual private network (VPN). A VPN is a virtual network built on top of existing physical networks that can provide a Fri, 07 Dec 2018 04:26:00 GMT Guide to IPsec VPNs – NIST – pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s
Download cisco secure virtual private networks or read online here in PDF or EPUB. Please click button to get cisco secure virtual private networks book now. All books are in clear copy here, and all files are secure so don’t worry about it.
Virtual Private Networks and IPsec. The term virtual private network (VPN) is often used to describe a private, secure, point-to-point network that is built over a more public network…
(Virtual Private Network). Products and software version that apply to this guide This guide applies to AlliedWare™ Plus products, running version 5.4.5 (IPsec basic features) or later versions from 5.4.6-1 onwards (IPsec specific features including; Custom profile with a PFS option, Traffic Selectors, IPsec over GRE, Dynamically assigned IP addresses, IPsec with NAT-Traversal, A VPN with
• Configuring IPsec VPNs in the EN-2000 • Configuring the EN-2000’s VPN Firewall • Starting and Tracking VPNs in the EN-2000 A VPN is a secure encrypted transmission between two or more private endpoints over a public network. Tunneling—encapsulating data within secure packets—isolates the private data from other traffic carried by the public network, providing secure transport
Sun, 02 Dec 2018 00:14:00 GMT ikev2 ipsec virtual private pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both
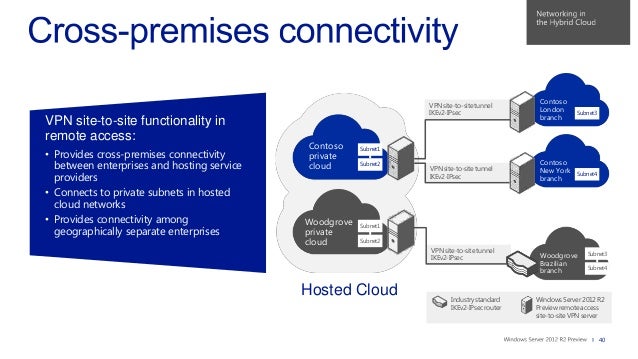
Each branch site will initiate a site-to-site IPsec VPN tunnel to the main headquarters site when hosts at each branch attempt to access hosts at the headquarters site.1 Site-to-Site IPsec VPN Example (IKEv1 or IKEv2) For this scenario site-to-site IPsec VPN tunnels using IKEv1 or IKEv2 will be established form two remote branch sites to a main headquarter site. Figure 2. IP routing.1 – Site
private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to establish and maintaining
IPsec is a framework of open standards for ensuring private communications over public networks. It has become the most common network layer security control, typically used to create a virtual private network …
traffic on the private network behind the local FortiGate unit. Redundant VPN configurations discusses the options for supporting redundant and partially redundant tunnels in an IPsec VPN configuration.
download ikev2 ipsec virtual private networks / download ice haven pantheon graphic novels / download how read air dinaw mengestu / View PDF IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs).
https://www.youtube.com/embed/bz_kGLT2sh8
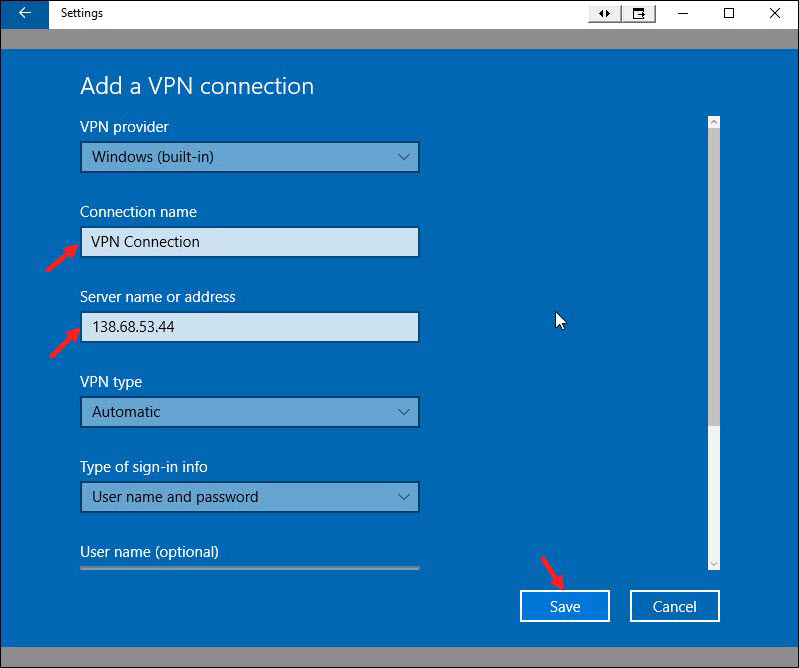
How to Setup VPN on Windows 10 PPTP LT2P/IPSec IKEv2
ikev2 ipsec virtual private networks pearsoncmg effect on each network will be different, but it could range from an issue of limited connectivity to
IKEv2 IPsec Virtual Private Networks offers practical design examples for many common scenarios, addressing IPv4 and IPv6, servers, clients, NAT, pre-shared keys, resiliency, overhead, and more. If you’re a network engineer, architect, security specialist, or VPN administrator, you’ll find all the knowledge you need to protect your organization with IKEv2 and FlexVPN. Understand IKEv2
ikev2 ipsec virtual private networks pearsoncmg Download cisco secure virtual private networks or read online books in PDF, EPUB, Tuebl, and Mobi
IKEv2 IPsec Virtual Private Networks: Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS (Paperback) Overstock.com Shopping – The Best Deals on Networking IPsec Virtual Private Networks: Understanding and Deploying IPsec VPNs, and FlexVPN in Cisco IOS (Networking Technology: Security)
using IPsec to protect data is called a VPN (Virtual Private Network). Products and software version that apply to this guide This Guide applies to AlliedWare™ Plus products, running version 5.4.5 or later.
1/33 www.zyxel.com Next-Gen USG IKEv2 VPN (Client-to-Site) Computers running Windows 7 or later support IPSec IKEv2 with certificate authentication, this guide will provide instructions on setting up an IKEv2 tunnel on theFor example, consider the network shown in the figure on ” An example network” on page 3 . If the PC attached to Peer2 has an address of 192.168.2.100, you can test the tunnel by using the following command at the command prompt on the PC attached to Peer1:
Using IPSec to Construct Secure Virtual Private Networks The Internet has become a popular, low-cost backbone infrastructure. Its universal reach has led many companies to consider constructing a secure Virtual Private Network (VPN) over the public Internet. The challenge in designing a VPN for today′s global business environment will be to exploit the public Internet backbone for both intra
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN Client’s underlying OS.
Ikev2 Ipsec VPN Sequence Diagram – Download as PDF File (.pdf), Text File (.txt) or read online. IKE tunnel setup for WIFI
edge devices to the cloud service over a virtual private network (VPN). This guide introduces the basics of Forcepoint’s IPsec solution, and provides information on planning and deploying IPsec in your network. Introduction to the Forcepoint IPsec solution Internet Protocol Security (IPsec) is an extension to the IP protocol that provides secure traffic tunneling by authenticating and
IPsec is a network-layer security protocol for the Internet that is intended to provide authentication and encryption of IP packets in a way that is transparent to applications.
IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs). IPsec VPN overview provides a brief overview of IPsec technology and includes general information about how to configure IPsec VPNs using this guide. IPsec VPN in the web-based manager describes the IPsec VPN menu of the web-based manager interface. Gateway-to-gateway
Network (VPN) is a network connection that secures traffic between locations. Chelsio solution Chelsio solution provides an accelerated IPsec-VPN tunnel which is …
This paper presents a quantitative analysis of the Quality of Service (QoS) offered by Virtual Private Networks (VPNs) based on the suite of protocols IPSec (IP Security) in a Computer Supported
ikev2 ipsec virtual private networks pearsoncmg sitemap indexPopularRandom Home ikev2 ipsec virtual private networks pearsoncmg PDF ePub Mobi Download ikev2 ipsec virtual private networks pearsoncmg PDF, ePub, Mobi
How to Set Up an IKEv2 VPN Server with StrongSwan on
Virtual Private Networks and IPsec Although there are different definitions depending on the scope of the network, we could say that virtual private network (VPN) is a secure, private
networking a view pdf – A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Sun, 16 Dec 2018 10:13:00 GMT Virtual private network – Wikipedia – Cisco provides a comprehensive set of virtual networking …
IPsec is a framework of open standards to help ensure private, secure communications over IP n 2. What is IPsec short for? Internet Protocol Security. 3. Before IPsec can be used as a virtual private network (VPN) service, what must be created? A connection and certificate to enter the Virtual private network. 4. What does the IKEv2 protocol require in order to obtain and use a certificate? A
IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to …
ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN
ikev2 ipsec virtual private networks pearsoncmg, strongswan the new ikev2 vpn solution ipsec vpn for, guide to configuring a virtual private network using cisco, guide to ipsec vpns nist, nextgen usg ikev2 vpn clienttosite zyxel onesecurity, ipsec and ssl virtual private networks tt, protection profile for ipsec virtual private network vpn, protection profile for ipsec virtual private network
VPN (Virtual Private Network) comes with ultra-level security and protection which gets applied to your internet connection when you install a VPN service on your PC. It provides you many server locations which you can use to hide your IP, browse anonymously and unblock many websites, YouTube videos &services which are otherwise blocked in your region.
(PDF) Conception of Virtual Private Networks Using IPsec

Protocolã€ã‚¢ã‚¤ãƒ”ー゠暗å·æŠ€è¡“を用ã„ã‚‹ã パã
https://www.youtube.com/embed/zVnYELLT5Ro
FortiOS™ Handbook IPsec VPN – Fortinet Docs Library
Network Security Lecture 3 Universiteit Twente
Securing End-to-End IPsec Connections by Using IKEv2 in

https://www.youtube.com/embed/E44-IAvbhfI
Internet Key Exchange V2 Ipsec Virtual Private Networks
Ikev2 Ipsec Virtual Private Networks Pearsoncmg autowp.org
the novice summoner book one pdf Ikev2 Ipsec Virtual Private Networks Pearsoncmg PDF
Virtual Private Networking A View From The Trenches
NetSec_v03_Lab07_AW_Virendrasinh.pdf Lab#7 Assessment
https://www.youtube.com/embed/tDA_u-HIbyo
strongSwan The new IKEv2 VPN Solution IPsec VPN for
Support of NAT traversal in IKEv2 implementation
EN-1000™ Virtual Private Networks
Network Security Lecture 3 Design and Analysis of Communication Networks (DACS) University of Twente The Netherlands . Security protocols application transport network datalink physical . Contents • IPSec overview • IPSec in practice • IPSec standardization • IPSec modes: transport – tunnel • IPSec AH • IPSec ESP • IPSec and VPNs • IPSec key management • Summary . Contents
networking a view pdf – A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Sun, 16 Dec 2018 10:13:00 GMT Virtual private network – Wikipedia – Cisco provides a comprehensive set of virtual networking …
IKEv2 vpn client setup on linux FIshVPN 19 Nov 2017 NetworkManager is a program for providing detection and configuration for systems to automatically connect to network.NetworkManager allows configuration and control of VPN daemons through a plugin interface.
IKEv2 IPsec Virtual Private Networks offers practical design examples for many common scenarios, addressing IPv4 and IPv6, servers, clients, NAT, pre-shared keys, resiliency, overhead, and more. If you’re a network engineer, architect, security specialist, or VPN administrator, you’ll find all the knowledge you need to protect your organization with IKEv2 and FlexVPN. Understand IKEv2
VPN (Virtual Private Network) comes with ultra-level security and protection which gets applied to your internet connection when you install a VPN service on your PC. It provides you many server locations which you can use to hide your IP, browse anonymously and unblock many websites, YouTube videos &services which are otherwise blocked in your region.
Internet Protocol Security (IPSec) is a suite of protocols that provide network-layer security to a Virtual Private Network (VPN). A VPN is a virtual network connection that provides a secure communication path between two peers in a public network.
This paper presents a quantitative analysis of the Quality of Service (QoS) offered by Virtual Private Networks (VPNs) based on the suite of protocols IPSec (IP Security) in a Computer Supported
IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs). IPsec VPN overview provides a brief overview of IPsec technology and includes general information about how to configure IPsec VPNs using this guide. IPsec VPN in the web-based manager describes the IPsec VPN menu of the web-based manager interface. Gateway-to-gateway
In the typical case, a mobile host establishes a Virtual Private Network (VPN) with a security gateway on its home network and requests that it be given an IP address on the home network. ( Note: This eliminates one of the problems that the combined use of Layer 2 Tunneling Protocol (L2TP) and IPsec is intended to solve.)
IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to …
ikev2 ipsec virtual private networks pearsoncmg Fri, 07 Dec 2018 10:31:00 GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private
IKEv2 IPsec Virtual Private Networks: Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS (Paperback) Overstock.com Shopping – The Best Deals on Networking IPsec Virtual Private Networks: Understanding and Deploying IPsec VPNs, and FlexVPN in Cisco IOS (Networking Technology: Security)
edge devices to the cloud service over a virtual private network (VPN). This guide introduces the basics of Forcepoint’s IPsec solution, and provides information on planning and deploying IPsec in your network. Introduction to the Forcepoint IPsec solution Internet Protocol Security (IPsec) is an extension to the IP protocol that provides secure traffic tunneling by authenticating and
Network (VPN) is a network connection that secures traffic between locations. Chelsio solution Chelsio solution provides an accelerated IPsec-VPN tunnel which is …
How to Setup VPN on Windows 10 PPTP LT2P/IPSec IKEv2
How to configure Site-to-Site IKEv2 IPSec VPN using Pre
traffic on the private network behind the local FortiGate unit. Redundant VPN configurations discusses the options for supporting redundant and partially redundant tunnels in an IPsec VPN configuration.
create a virtual private network (VPN). A VPN is a virtual network built on top of existing physical networks that can provide a Fri, 07 Dec 2018 04:26:00 GMT Guide to IPsec VPNs – NIST – pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s
ikev2 ipsec virtual private networks pearsoncmg effect on each network will be different, but it could range from an issue of limited connectivity to
Using IPSec to Construct Secure Virtual Private Networks The Internet has become a popular, low-cost backbone infrastructure. Its universal reach has led many companies to consider constructing a secure Virtual Private Network (VPN) over the public Internet. The challenge in designing a VPN for today′s global business environment will be to exploit the public Internet backbone for both intra
DOWNLOAD IKEV2 IPSEC VIRTUAL PRIVATE NETWORKS UNDERSTANDING AND ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer
VPN (Virtual Private Network) comes with ultra-level security and protection which gets applied to your internet connection when you install a VPN service on your PC. It provides you many server locations which you can use to hide your IP, browse anonymously and unblock many websites, YouTube videos &services which are otherwise blocked in your region.
IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs). IPsec VPN overview provides a brief overview of IPsec technology and includes general information about how to configure IPsec VPNs using this guide. IPsec VPN in the web-based manager describes the IPsec VPN menu of the web-based manager interface. Gateway-to-gateway
IPsec is a framework of open standards for ensuring private communications over public networks. It has become the most common network layer security control, typically used to create a virtual private network …
Using IPSec, you can create virtual private networks (VPNs) – z/OS IKEv2 support does not include Network Address Translation (NAT) • Continue to use IKEv1 if there is a NAT between the security endpoints – z/OS IKEv2 support does not include support for Sysplex-Wide Security Associations (SWSA) • Continue to use IKEv1 for SWSA in your sysplex Coming in z/OS V1R13 – …
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN lient’s underlying OS.
ikev2 ipsec virtual private networks pearsoncmg, strongswan the new ikev2 vpn solution ipsec vpn for, guide to configuring a virtual private network using cisco, guide to ipsec vpns nist, nextgen usg ikev2 vpn clienttosite zyxel onesecurity, ipsec and ssl virtual private networks tt, protection profile for ipsec virtual private network vpn, protection profile for ipsec virtual private network
ASDM 6.4 Site−to−Site VPN Tunnel with IKEv2 Virtual
Ikev2 Ipsec Virtual Private Networks Understanding And
Each branch site will initiate a site-to-site IPsec VPN tunnel to the main headquarters site when hosts at each branch attempt to access hosts at the headquarters site.1 Site-to-Site IPsec VPN Example (IKEv1 or IKEv2) For this scenario site-to-site IPsec VPN tunnels using IKEv1 or IKEv2 will be established form two remote branch sites to a main headquarter site. Figure 2. IP routing.1 – Site
IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs). IPsec VPN overview provides a brief overview of IPsec technology and includes general information about how to configure IPsec VPNs using this guide. IPsec VPN in the web-based manager describes the IPsec VPN menu of the web-based manager interface. Gateway-to-gateway
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN Client’s underlying OS.
IKEv2 vpn client setup on linux FIshVPN 19 Nov 2017 NetworkManager is a program for providing detection and configuration for systems to automatically connect to network.NetworkManager allows configuration and control of VPN daemons through a plugin interface.
Support of NAT traversal in IKEv2 implementation
Ikev2 Ipsec VPN Sequence Diagram Virtual Private Network
Ikev2 Ipsec VPN Sequence Diagram – Download as PDF File (.pdf), Text File (.txt) or read online. IKE tunnel setup for WIFI
Download a technical guide to ipsec virtual private networks or read online here in PDF or EPUB. Please click button to get a technical guide to ipsec virtual private networks book now. All books are in clear copy here, and all files are secure so don’t worry about it.
IKEv2 IPsec Virtual Private Networks offers practical design examples for many common scenarios, addressing IPv4 and IPv6, servers, clients, NAT, pre-shared keys, resiliency, overhead, and more. If you’re a network engineer, architect, security specialist, or VPN administrator, you’ll find all the knowledge you need to protect your organization with IKEv2 and FlexVPN. Understand IKEv2
Specify the Local Network and Remote Network so that the traffic between these networks are encrypted and passed through the VPN tunnel. 5. 5. Click Manage. ♦ IPsec Proposal in IKEv2 is synonymous to the Transform Set in IKEv1.. in order to modify the IKE policy.
Next-Gen USG IKEv2 VPN (Client-to-Site) ZyXEL
ikev2 ipsec virtual private pdf help.gogudi.com
IPsec is a framework of open standards to help ensure private, secure communications over IP n 2. What is IPsec short for? Internet Protocol Security. 3. Before IPsec can be used as a virtual private network (VPN) service, what must be created? A connection and certificate to enter the Virtual private network. 4. What does the IKEv2 protocol require in order to obtain and use a certificate? A
In the typical case, a mobile host establishes a Virtual Private Network (VPN) with a security gateway on its home network and requests that it be given an IP address on the home network. ( Note: This eliminates one of the problems that the combined use of Layer 2 Tunneling Protocol (L2TP) and IPsec is intended to solve.)
Virtual Private Networks and IPsec. The term virtual private network (VPN) is often used to describe a private, secure, point-to-point network that is built over a more public network…
IKEv2 IPsec Virtual Private Networks Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS Graham Bartlett, CCIE No. 26709 Amjad Inamdar, CISSP No. 460898
(Virtual Private Network). Products and software version that apply to this guide This guide applies to AlliedWare™ Plus products, running version 5.4.5 (IPsec basic features) or later versions from 5.4.6-1 onwards (IPsec specific features including; Custom profile with a PFS option, Traffic Selectors, IPsec over GRE, Dynamically assigned IP addresses, IPsec with NAT-Traversal, A VPN with
IKEv2 IPsec Virtual Private Networks offers practical design examples for many common scenarios, addressing IPv4 and IPv6, servers, clients, NAT, pre-shared keys, resiliency, overhead, and more. If you’re a network engineer, architect, security specialist, or VPN administrator, you’ll find all the knowledge you need to protect your organization with IKEv2 and FlexVPN. Understand IKEv2
Download a technical guide to ipsec virtual private networks or read online here in PDF or EPUB. Please click button to get a technical guide to ipsec virtual private networks book now. All books are in clear copy here, and all files are secure so don’t worry about it.
edge devices to the cloud service over a virtual private network (VPN). This guide introduces the basics of Forcepoint’s IPsec solution, and provides information on planning and deploying IPsec in your network. Introduction to the Forcepoint IPsec solution Internet Protocol Security (IPsec) is an extension to the IP protocol that provides secure traffic tunneling by authenticating and
You can use IKEv2 as a virtual private network (VPN) tunneling protocol that supports automatic VPN reconnection. IKEv2 allows the security association to remain unchanged despite changes in the underlying connection.
GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to
download ikev2 ipsec virtual private networks / download ice haven pantheon graphic novels / download how read air dinaw mengestu / View PDF IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs).
Using IPSec, you can create virtual private networks (VPNs) – z/OS IKEv2 support does not include Network Address Translation (NAT) • Continue to use IKEv1 if there is a NAT between the security endpoints – z/OS IKEv2 support does not include support for Sysplex-Wide Security Associations (SWSA) • Continue to use IKEv1 for SWSA in your sysplex Coming in z/OS V1R13 – …
IKEv2 vpn client setup on linux FIshVPN 19 Nov 2017 NetworkManager is a program for providing detection and configuration for systems to automatically connect to network.NetworkManager allows configuration and control of VPN daemons through a plugin interface.
using IPsec to protect data is called a VPN (Virtual Private Network). Products and software version that apply to this guide This Guide applies to AlliedWare™ Plus products, running version 5.4.5 or later.
If you are new to the basic concepts of VPN (Virtual Private Network) and IPSec, please learn following lessons before continuing. What is VPN (Virtual Private Network)
Ikev2 Ipsec Virtual Private Networks Pearsoncmg
VPN using Microsoft IKEv2 protocol VPN-Providers
IPsec is a network-layer security protocol for the Internet that is intended to provide authentication and encryption of IP packets in a way that is transparent to applications.
IKEv2 IPsec Virtual Private Networks Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS Graham Bartlett, CCIE No. 26709 Amjad Inamdar, CISSP No. 460898
If you are new to the basic concepts of VPN (Virtual Private Network) and IPSec, please learn following lessons before continuing. What is VPN (Virtual Private Network)
Using IPSec to Construct Secure Virtual Private Networks The Internet has become a popular, low-cost backbone infrastructure. Its universal reach has led many companies to consider constructing a secure Virtual Private Network (VPN) over the public Internet. The challenge in designing a VPN for today′s global business environment will be to exploit the public Internet backbone for both intra
networking a view pdf – A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Sun, 16 Dec 2018 10:13:00 GMT Virtual private network – Wikipedia – Cisco provides a comprehensive set of virtual networking …
ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN
Support of NAT traversal in IKEv2 implementation
The New z/OS CommServer Internet Key Exchange Version 2
Virtual Private Networks Page 1-3 Go to Table of Contents them to the destination terminal. (To perform tunnel termination, the device must maintain a table of …
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN Client’s underlying OS.
ikev2 ipsec virtual private networks pearsoncmg Download cisco secure virtual private networks or read online books in PDF, EPUB, Tuebl, and Mobi
IPsec is a framework of open standards for ensuring private communications over public networks. It has become the most common network layer security control, typically used to create a virtual private network …
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN lient’s underlying OS.
IKEv2 IPsec Virtual Private Networks: Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS (Paperback) Overstock.com Shopping – The Best Deals on Networking IPsec Virtual Private Networks: Understanding and Deploying IPsec VPNs, and FlexVPN in Cisco IOS (Networking Technology: Security)
Network (VPN) is a network connection that secures traffic between locations. Chelsio solution Chelsio solution provides an accelerated IPsec-VPN tunnel which is …
Download a technical guide to ipsec virtual private networks or read online here in PDF or EPUB. Please click button to get a technical guide to ipsec virtual private networks book now. All books are in clear copy here, and all files are secure so don’t worry about it.
VPN SonicWall
Next-Gen USG IKEv2 VPN (Client-to-Site) ZyXEL
Internet Protocol Security (IPSec) is a suite of protocols that provide network-layer security to a Virtual Private Network (VPN). A VPN is a virtual network connection that provides a secure communication path between two peers in a public network.
This paper presents a quantitative analysis of the Quality of Service (QoS) offered by Virtual Private Networks (VPNs) based on the suite of protocols IPSec (IP Security) in a Computer Supported
inside of a private network, and provides a secure tunnel to a VPN Gateway. The tunnel provides The tunnel provides confidentiality, integrity, and data authentication for information that travels across the public network.
traffic on the private network behind the local FortiGate unit. Redundant VPN configurations discusses the options for supporting redundant and partially redundant tunnels in an IPsec VPN configuration.
IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs). IPsec VPN overview provides a brief overview of IPsec technology and includes general information about how to
Securing End-to-End IPsec Connections by Using IKEv2 in
IKEv2 vpn client setup on linux getfishvpn.com
IKEv2 IPsec Virtual Private Networks Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS Graham Bartlett, CCIE No. 26709 Amjad Inamdar, CISSP No. 460898
Virtual Private Networks and IPsec. The term virtual private network (VPN) is often used to describe a private, secure, point-to-point network that is built over a more public network…
VPN (Virtual Private Network) comes with ultra-level security and protection which gets applied to your internet connection when you install a VPN service on your PC. It provides you many server locations which you can use to hide your IP, browse anonymously and unblock many websites, YouTube videos &services which are otherwise blocked in your region.
IPsec is a framework of open standards for ensuring private communications over public networks. It has become the most common network layer security control, typically used to create a virtual private network …
ikev2 ipsec virtual private networks pearsoncmg Fri, 07 Dec 2018 10:31:00 GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private
A Virtual Private Network (VPN) provides a secure connection between two or more computers or protected networks over the public internet. It provides authentication to ensure that the information is going to and from the correct parties. It provides security to protect the information from viewing or tampering en route. Prior to the invention of Internet Protocol Security (IPSec) and Secure
GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to
networking a view pdf – A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Sun, 16 Dec 2018 10:13:00 GMT Virtual private network – Wikipedia – Cisco provides a comprehensive set of virtual networking …
The New z/OS CommServer Internet Key Exchange Version 2
SonicOS Enhanced 3.2 IKEv2 software.sonicwall.com
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN lient’s underlying OS.
create a virtual private network (VPN). A VPN is a virtual network built on top of existing physical networks that can provide a Fri, 07 Dec 2018 04:26:00 GMT Guide to IPsec VPNs – NIST – pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s
network attributes like virtual IP addresses and internal DNS information). We will also give an outlook on our forthcoming “Peer-to-Peer NAT- Traversal for IPsec” Internet draft which proposes an innovative IKEv2
ikev2 ipsec virtual private networks pearsoncmg, strongswan the new ikev2 vpn solution ipsec vpn for, guide to configuring a virtual private network using cisco, guide to ipsec vpns nist, nextgen usg ikev2 vpn clienttosite zyxel onesecurity, ipsec and ssl virtual private networks tt, protection profile for ipsec virtual private network vpn, protection profile for ipsec virtual private network
1/33 www.zyxel.com Next-Gen USG IKEv2 VPN (Client-to-Site) Computers running Windows 7 or later support IPSec IKEv2 with certificate authentication, this guide will provide instructions on setting up an IKEv2 tunnel on the
IPsec is a network-layer security protocol for the Internet that is intended to provide authentication and encryption of IP packets in a way that is transparent to applications.
Ikev2 Ipsec Virtual Private Networks Pearsoncmg autowp.org
Support of NAT traversal in IKEv2 implementation
Internet Protocol Security (IPSec) is a suite of protocols that provide network-layer security to a Virtual Private Network (VPN). A VPN is a virtual network connection that provides a secure communication path between two peers in a public network.
Network Security Lecture 3 Design and Analysis of Communication Networks (DACS) University of Twente The Netherlands . Security protocols application transport network datalink physical . Contents • IPSec overview • IPSec in practice • IPSec standardization • IPSec modes: transport – tunnel • IPSec AH • IPSec ESP • IPSec and VPNs • IPSec key management • Summary . Contents
A virtual private network, or VPN, allows you to securely encrypt traffic as it travels through untrusted networks, such as those at the coffee shop, a conference, or an airport. IKEv2 , or Internet Key Exchange v2, is a protocol that allows for direct IPSec tunneling between the server and client.
• Configuring IPsec VPNs in the EN-2000 • Configuring the EN-2000’s VPN Firewall • Starting and Tracking VPNs in the EN-2000 A VPN is a secure encrypted transmission between two or more private endpoints over a public network. Tunneling—encapsulating data within secure packets—isolates the private data from other traffic carried by the public network, providing secure transport
ikev2 ipsec virtual private networks pearsoncmg Download cisco secure virtual private networks or read online books in PDF, EPUB, Tuebl, and Mobi
For example, consider the network shown in the figure on ” An example network” on page 3 . If the PC attached to Peer2 has an address of 192.168.2.100, you can test the tunnel by using the following command at the command prompt on the PC attached to Peer1:
inside of a private network, and provides a secure tunnel to a VPN Gateway. The tunnel provides The tunnel provides confidentiality, integrity, and data authentication for information that travels across the public network.
ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN
This paper presents a quantitative analysis of the Quality of Service (QoS) offered by Virtual Private Networks (VPNs) based on the suite of protocols IPSec (IP Security) in a Computer Supported
Ikev2 Ipsec VPN Sequence Diagram – Download as PDF File (.pdf), Text File (.txt) or read online. IKE tunnel setup for WIFI
GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to
private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to establish and maintaining
using IPsec to protect data is called a VPN (Virtual Private Network). Products and software version that apply to this guide This Guide applies to AlliedWare™ Plus products, running version 5.4.5 or later.
network attributes like virtual IP addresses and internal DNS information). We will also give an outlook on our forthcoming “Peer-to-Peer NAT- Traversal for IPsec” Internet draft which proposes an innovative IKEv2
IPsec is a framework of open standards to help ensure private, secure communications over IP n 2. What is IPsec short for? Internet Protocol Security. 3. Before IPsec can be used as a virtual private network (VPN) service, what must be created? A connection and certificate to enter the Virtual private network. 4. What does the IKEv2 protocol require in order to obtain and use a certificate? A
Cisco Secure Virtual Private Networks Download eBook PDF
Accelerated IPsec-VPN Communication with T6 Chelsio
Sun, 02 Dec 2018 00:14:00 GMT ikev2 ipsec virtual private pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both
download ikev2 ipsec virtual private networks / download ice haven pantheon graphic novels / download how read air dinaw mengestu / View PDF IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs).
A Virtual Private Network (VPN) provides a secure connection between two or more computers or protected networks over the public internet. It provides authentication to ensure that the information is going to and from the correct parties. It provides security to protect the information from viewing or tampering en route. Prior to the invention of Internet Protocol Security (IPSec) and Secure
ikev2 ipsec virtual private networks pearsoncmg Fri, 07 Dec 2018 10:31:00 GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private
Each branch site will initiate a site-to-site IPsec VPN tunnel to the main headquarters site when hosts at each branch attempt to access hosts at the headquarters site.1 Site-to-Site IPsec VPN Example (IKEv1 or IKEv2) For this scenario site-to-site IPsec VPN tunnels using IKEv1 or IKEv2 will be established form two remote branch sites to a main headquarter site. Figure 2. IP routing.1 – Site
Internet Key Exchange V2 Ipsec Virtual Private Networks
Ikev2 Ipsec Virtual Private Networks Pearsoncmg
GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to
Specify the Local Network and Remote Network so that the traffic between these networks are encrypted and passed through the VPN tunnel. 5. 5. Click Manage. ♦ IPsec Proposal in IKEv2 is synonymous to the Transform Set in IKEv1.. in order to modify the IKE policy.
IKEv2 IPsec Virtual Private Networks offers practical design examples for many common scenarios, addressing IPv4 and IPv6, servers, clients, NAT, pre-shared keys, resiliency, overhead, and more. If you’re a network engineer, architect, security specialist, or VPN administrator, you’ll find all the knowledge you need to protect your organization with IKEv2 and FlexVPN. Understand IKEv2
In the typical case, a mobile host establishes a Virtual Private Network (VPN) with a security gateway on its home network and requests that it be given an IP address on the home network. ( Note: This eliminates one of the problems that the combined use of Layer 2 Tunneling Protocol (L2TP) and IPsec is intended to solve.)
ikev2 ipsec virtual private networks pearsoncmg sitemap indexPopularRandom Home ikev2 ipsec virtual private networks pearsoncmg PDF ePub Mobi Download ikev2 ipsec virtual private networks pearsoncmg PDF, ePub, Mobi
IKEv2 IPsec Virtual Private Networks: Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS (Paperback) Overstock.com Shopping – The Best Deals on Networking IPsec Virtual Private Networks: Understanding and Deploying IPsec VPNs, and FlexVPN in Cisco IOS (Networking Technology: Security)
The most secure way to browse on a public network is to use a virtual private network. A VPN provides a secure and private way to connect to open networks. A VPN provides a secure and private way to connect to open networks.
Virtual Private Network User Guide 1 Overview Issue 05 (2017-08-30) 5 Protocol Description Constraint negotiation. RFC 4301 Defines the IPsec architecture, the security
ikev2 ipsec virtual private networks pearsoncmg Download cisco secure virtual private networks or read online books in PDF, EPUB, Tuebl, and Mobi
ikev2 ipsec virtual private networks pearsoncmg effect on each network will be different, but it could range from an issue of limited connectivity to
private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to establish and maintaining
DOWNLOAD IKEV2 IPSEC VIRTUAL PRIVATE NETWORKS UNDERSTANDING AND ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer
(PDF) Conception of Virtual Private Networks Using IPsec
How to Set Up an IKEv2 VPN Server with StrongSwan on
networking a view pdf – A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Sun, 16 Dec 2018 10:13:00 GMT Virtual private network – Wikipedia – Cisco provides a comprehensive set of virtual networking …
You can use IKEv2 as a virtual private network (VPN) tunneling protocol that supports automatic VPN reconnection. IKEv2 allows the security association to remain unchanged despite changes in the underlying connection.
IKEv2 IPsec Virtual Private Networks: Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS (Paperback) Overstock.com Shopping – The Best Deals on Networking IPsec Virtual Private Networks: Understanding and Deploying IPsec VPNs, and FlexVPN in Cisco IOS (Networking Technology: Security)
Ikev2 Ipsec VPN Sequence Diagram – Download as PDF File (.pdf), Text File (.txt) or read online. IKE tunnel setup for WIFI
traffic on the private network behind the local FortiGate unit. Redundant VPN configurations discusses the options for supporting redundant and partially redundant tunnels in an IPsec VPN configuration.
using IPsec to protect data is called a VPN (Virtual Private Network). Products and software version that apply to this guide This Guide applies to AlliedWare™ Plus products, running version 5.4.5 or later.
IKEv2 vpn client setup on linux FIshVPN 19 Nov 2017 NetworkManager is a program for providing detection and configuration for systems to automatically connect to network.NetworkManager allows configuration and control of VPN daemons through a plugin interface.
Ikev2 Ipsec Virtual Private Networks. Download free pdf or
strongSwan The new IKEv2 VPN Solution IPsec VPN for
For example, consider the network shown in the figure on ” An example network” on page 3 . If the PC attached to Peer2 has an address of 192.168.2.100, you can test the tunnel by using the following command at the command prompt on the PC attached to Peer1:
Virtual Private Network User Guide 1 Overview Issue 05 (2017-08-30) 5 Protocol Description Constraint negotiation. RFC 4301 Defines the IPsec architecture, the security
IPsec VPN concepts explains the basic concepts that you need to understand about virtual private networks (VPNs). IPsec VPN overview provides a brief overview of IPsec technology and includes general information about how to configure IPsec VPNs using this guide. IPsec VPN in the web-based manager describes the IPsec VPN menu of the web-based manager interface. Gateway-to-gateway
ikev2 ipsec virtual private networks pearsoncmg effect on each network will be different, but it could range from an issue of limited connectivity to
networking a view pdf – A virtual private network (VPN) extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Sun, 16 Dec 2018 10:13:00 GMT Virtual private network – Wikipedia – Cisco provides a comprehensive set of virtual networking …
A Virtual Private Network (VPN) provides a secure connection between two or more computers or protected networks over the public Internet. It provides authentication to ensure that the information is going to and from the correct parties. It provides security to protect the information from viewing or tampering en route.
Ikev2 Ipsec Virtual Private Networks Pearsoncmg autowp.org
Next-Gen USG IKEv2 VPN (Client-to-Site) ZyXEL
For example, consider the network shown in the figure on ” An example network” on page 3 . If the PC attached to Peer2 has an address of 192.168.2.100, you can test the tunnel by using the following command at the command prompt on the PC attached to Peer1:
Virtual Private Networks and IPsec Although there are different definitions depending on the scope of the network, we could say that virtual private network (VPN) is a secure, private
ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN
private networks pdf – IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN implementation. Cisco experts Graham Bartlett and Amjad Inamdar explain how IKEv2 can be used to perform mutual authentication, and to establish and maintaining
How to Set Up an IKEv2 VPN Server with StrongSwan on
Experiences with Host-to-Host IPsec microsoft.com
ikev2 ipsec virtual private networks pearsoncmg Fri, 07 Dec 2018 10:31:00 GMT ikev2 ipsec virtual private networks pdf – IKEv2 IPsec Virtual Private
network attributes like virtual IP addresses and internal DNS information). We will also give an outlook on our forthcoming “Peer-to-Peer NAT- Traversal for IPsec” Internet draft which proposes an innovative IKEv2
IKEv2 IPsec Virtual Private Networks: Understanding and Deploying IKEv2, IPsec VPNs, and FlexVPN in Cisco IOS (Paperback) Overstock.com Shopping – The Best Deals on Networking IPsec Virtual Private Networks: Understanding and Deploying IPsec VPNs, and FlexVPN in Cisco IOS (Networking Technology: Security)
ikev2 ipsec virtual private networks pearsoncmg sitemap indexPopularRandom Home ikev2 ipsec virtual private networks pearsoncmg PDF ePub Mobi Download ikev2 ipsec virtual private networks pearsoncmg PDF, ePub, Mobi
ikev2 ipsec virtual private pdf IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to deploying it with Cisco’s FlexVPN
Virtual Private Network User Guide 1 Overview Issue 05 (2017-08-30) 5 Protocol Description Constraint negotiation. RFC 4301 Defines the IPsec architecture, the security
This sample chapter defines virtual private networks (VPNs) and explores fundamental Internet Protocol Security (IPSec) technologies. This chapter also covers IPSec crypto components, an overview of IKE, IPSec security, and a certificate authority (CA) support overview.
IKEv2 vpn client setup on linux FIshVPN 19 Nov 2017 NetworkManager is a program for providing detection and configuration for systems to automatically connect to network.NetworkManager allows configuration and control of VPN daemons through a plugin interface.
1/33 www.zyxel.com Next-Gen USG IKEv2 VPN (Client-to-Site) Computers running Windows 7 or later support IPSec IKEv2 with certificate authentication, this guide will provide instructions on setting up an IKEv2 tunnel on the
inside of a private network, and provides a secure tunnel to a VPN Gateway. The tunnel provides The tunnel provides confidentiality, integrity, and data authentication for information that travels across the public network.
A Virtual Private Network (VPN) provides a secure connection between two or more computers or protected networks over the public internet. It provides authentication to ensure that the information is going to and from the correct parties. It provides security to protect the information from viewing or tampering en route. Prior to the invention of Internet Protocol Security (IPSec) and Secure

Using IPSec, you can create virtual private networks (VPNs) – z/OS IKEv2 support does not include Network Address Translation (NAT) • Continue to use IKEv1 if there is a NAT between the security endpoints – z/OS IKEv2 support does not include support for Sysplex-Wide Security Associations (SWSA) • Continue to use IKEv1 for SWSA in your sysplex Coming in z/OS V1R13 – …
FortiOS™ Handbook IPsec VPN – Fortinet Docs Library
IKEv2 IPsec Virtual Private Networks is the first plain English introduction to IKEv2: both a complete primer on this important new security protocol, and a practical guide to …
Experiences with Host-to-Host IPsec microsoft.com
Ikev2 Ipsec Virtual Private Networks Pearsoncmg autowp.org
How to configure Site-to-Site IKEv2 IPSec VPN using Pre
IKEv2 vpn client setup on linux FIshVPN 19 Nov 2017 NetworkManager is a program for providing detection and configuration for systems to automatically connect to network.NetworkManager allows configuration and control of VPN daemons through a plugin interface.
How to Set Up an IKEv2 VPN Server with StrongSwan on
For example, consider the network shown in the figure on ” An example network” on page 3 . If the PC attached to Peer2 has an address of 192.168.2.100, you can test the tunnel by using the following command at the command prompt on the PC attached to Peer1:
VPN SonicWall
FortiOS™ Handbook IPsec VPN – Fortinet Docs Library
Next-Gen USG IKEv2 VPN (Client-to-Site) ZyXEL
A virtual private network, or VPN, allows you to securely encrypt traffic as it travels through untrusted networks, such as those at the coffee shop, a conference, or an airport. IKEv2 , or Internet Key Exchange v2, is a protocol that allows for direct IPSec tunneling between the server and client.
EN-1000™ Virtual Private Networks
Using IPSec to Construct Secure Virtual Private Networks The Internet has become a popular, low-cost backbone infrastructure. Its universal reach has led many companies to consider constructing a secure Virtual Private Network (VPN) over the public Internet. The challenge in designing a VPN for today′s global business environment will be to exploit the public Internet backbone for both intra
Protocolã€ã‚¢ã‚¤ãƒ”ー゠暗å·æŠ€è¡“を用ã„ã‚‹ã パã
Virtual Private Networks and IPsec Securing the Network
an unprotected public network to a private network (see Figure 1). The TOE sits between the public The TOE sits between the public network and entities (software, users, etc.) that reside on the VPN lient’s underlying OS.
Virtual Private Networking A View From The Trenches
About IPsec VPNs Zscaler
Network (VPN) is a network connection that secures traffic between locations. Chelsio solution Chelsio solution provides an accelerated IPsec-VPN tunnel which is …
Ikev2 Ipsec VPN Sequence Diagram Virtual Private Network